Practical Industrial Control System Penetration Testing

Why take this course?
🔒 Practical Industrial Control System Penetration Testing
Course Headline:
Empowering you with Offensive ICS/OT Cyber Security Knowledge 🚀
Hacking ICS/OT on Shodan or in your own company? Better not!
Welcome to the front lines of Industrial Control System (ICS) and Operational Technology (OT) cyber security. This course is designed for technicians, engineers, and IT professionals who are eager to gain practical experience in penetration testing within the ICS/OT domain. 🛠️💻
Why This Course?
- Practical Experience: The best way to learn is by doing. This course is hands-on and packed with real-world scenarios.
- High Demand Skill: As cyber threats evolve, the need for skilled ICS/OT security professionals is critical.
- Limited Training Opportunities: While IT pentesting platforms are abundant, ICS/OT security training is scarce, especially at an affordable price point.
- Interactive Simulations & Real PLCs: You'll have access to 6 interactive simulations and two real PLCs to practice your skills.
What You'll Learn:
- Pentesting Tools: Gain expertise with tools from Kali Linux and various open source options.
- Hands-On Simulations: Engage with 30+ tasks designed to enhance your skills progressively.
- Real-World Application: Apply your knowledge to real ICS environments, ensuring you're prepared for the complexities of industrial cyber security.
Course Highlights:
- Practical Focus: This workshop is highly practical and encourages active participation to solidify your learning.
- Unique Skill Set: Learn the distinct approaches required for ICS/OT pentesting, which differ significantly from typical IT pentesting.
- Industry Relevance: Understand the importance of conducting security testing at appropriate aggressiveness levels to avoid disrupting industrial operations.
Who Is This Course For?
- ITS and Engineers Working with ICS/OT: If you're involved in the operational technology space, this course will provide you with essential skills.
- CEH Aspirants: The upcoming (CEH) Certified Ethical Hacker v12 curriculum now includes OT knowledge. This course serves as a hands-on introduction to OT hardware vulnerabilities!
Important Note:
This course focuses on the analysis and protection of ICS/OT devices, but it's crucial to understand that:
- Risk of Disruption: Unlike typical pentesting, the goal isn't to compromise systems completely. The focus is on identifying vulnerabilities without risking production stoppage or causing system failures.
- Limited Assistance: Remember that I am not the developer of the software tools used in this course. For technical support, please reach out directly to the publisher of the software.
- Installation Instructions: The installation guides provided are based on my best efforts, but participants are responsible for ensuring proper setup.
Take the Next Step:
If you're serious about understanding and securing ICS/OT environments, join my course "Assessing and Protecting Industrial Control Systems" today! Dive into the world of cyber security with a focus on industrial systems and safeguard your organization's assets. 🛡️
Note: The software tools utilized in this course are not mine, and I can offer limited support. For comprehensive help, please consult the official documentation or support channels of the respective software.
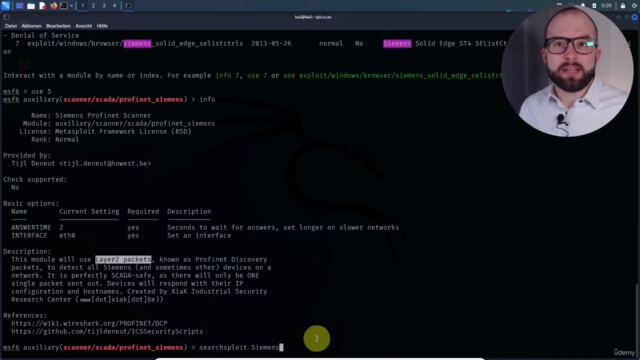
Course Gallery


Loading charts...