Mobile Application Hacking and Penetration Testing (Android)

Why take this course?
🛡️ Master Mobile Application Hacking and Penetration Testing with Expert Eslam Medhat!
Course Overview:
Dive into the world of Android mobile application security with our comprehensive course, designed to equip you with the skills needed to excel in the field of Cyber Security. This isn't just a course; it's your gateway to understanding how to perform thorough Penetration Testing on Android apps. 📱
What You'll Learn:
- Foundations of Android Architecture: Gain a solid understanding of how Android operates, from the basics to the advanced.
- Reverse Engineering Mastery: Learn the techniques and tools required to reverse engineer mobile applications effectively.
- Practical Application: Engage with real-world mobile applications in a hands-on approach.
- Build Your Own Lab: Create a home lab focused on mobile application security, giving you the power to test and learn at your own pace.
- Penetration Testing Skills: Acquire the practical skills needed to conduct comprehensive Penetration tests on mobile applications.
Course Highlights:
- Comprehensive Syllabus: Our syllabus covers everything from the basics of mobile apps to advanced topics like OWASP top 10 vulnerabilities for mobiles.
- Detailed Modules: We'll walk you through the AndroidManifest.xml file, the compilation and startup processes, and the various components that make up an Android app.
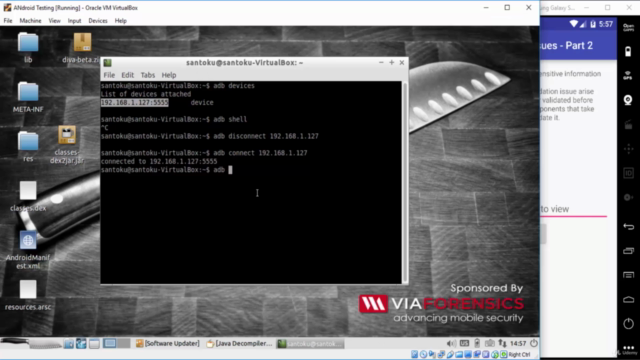
- Setting Up Your Testing Environment: Learn how to set up a testing environment using tools like the Android Debug Bridge (adb) and DIVA (Damn insecure and vulnerable App).
- In-Depth Analysis: Discover how to intercept, analyze, and exploit network traffic, and understand how to reverse an Android application to uncover security vulnerabilities.
- Real-World Practice: Work on real-world applications to apply what you've learned in a practical environment.
Course Syllabus:
- Introduction To Mobile Apps
- Mobile Application Security Fundamentals
- Mobile Application Penetration Testing Methodologies
- Common Data Storage Areas and Security Concerns
- The Architecture of Android Applications
- Android App Sandbox and Permission Model
- Analyzing the AndroidManifest.xml File
- Understanding the Android Compilation Process
- Exploring the Android Startup Process
- Dissecting Android Application Components
- Setting Up a Testing Environment for Mobile Apps
- Android Debug Bridge (adb) Explained
- Deep Dive into Android with ADB Tools
- Network Traffic Analysis
- Reverse Engineering Android Applications
- OWASP Top 10 Vulnerabilities for Mobile Platforms
- Working with DIVA (Damn insecure and vulnerable App)
- Insecure Logging Issues
- Insecure Data Storage Concerns
- Database Insecure Storage Practices
- Temporary File Storage Vulnerabilities
- Hardcoding Security Flaws
- Input Validation and SQL Injection Attacks
- Exploiting Webview Vulnerabilities
Unmatched Support:
You'll receive 24/7 course support, so whenever you have questions or need guidance, our team is here to respond within 10 hours. Our community is your best resource for overcoming challenges and accelerating your learning journey.
Ethical Note:
This course is intended solely for educational purposes. It is designed to help you understand the importance of mobile application security and how to protect against vulnerabilities, not to exploit them unethically. Join us in responsible learning and becoming a cybersecurity champion! 🛡️💻
Embark on your journey to become a master of Mobile Application Hacking and Penetration Testing today with Eslam Medhat's expert guidance. Enroll now and secure your future in the world of Cyber Security! 🚀🌟
Course Gallery


Loading charts...